Cybercriminals possibly view every company today as a glass house. All those shiny digital systems, customer databases, internal tools, cloud setups. They look solid on the outside but quite attractive, prime target for cyberattacks.
This is because one well-aimed stone (or cyberattack in this case) can crack the entire structure. And if you’ve ever overseen business system protection, you know that uneasy feeling: What if someone’s already poking at the walls we can’t see?
This is exactly where penetration testing makes life a bit easy. The process of letting professionals—yes, ethical hackers—try to break into your systems the way a real criminal would. It cracks open the opportunity to discover gaps after an actual breach.
The Role of Ethical Hackers
Ethical hackers aren’t out there to hurt your company. They take your necessary permissions, and they are on your side.
Unlike malicious attackers, ethical hackers document everything. They’ll tell you which locks are weak, which windows don’t shut properly, and which backdoor you didn’t even realize existed. In corporate language, that means identifying security flaws before attackers exploit them.
And it’s not just about running tools. It’s about creativity. Real-world attackers don’t follow a script. They adapt. Ethical hackers do the same mirroring the unpredictable nature of cybercrime but without the consequences.
Why Penetration Testing Matters More Than Ever
If you’re managing IT or security today, you already know patching vulnerabilities feels like chasing shadows. New threats pop up faster than you can fix the old ones. Firewalls and antivirus software are helpful but not so much.
Penetration testing is different. It doesn’t wait for an alert. It actively challenges your defences. It’s rehearsal, practice and stress-test all rolled into one.
The outcome? You don’t just get a list of “what’s wrong.” You get a roadmap of how an attacker would move step by step—from reconnaissance to exploitation to escalation. That knowledge is priceless because it helps you build stronger defences that are grounded in reality and not theory.
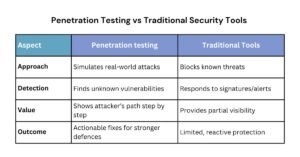
Comparison Chart – Penetration Testing vs Traditional Security Tools
How Ethical Hackers Simulate Real-World Attacks
Let’s break it down. A typical penetration testing engagement often moves through phases that look eerily similar to how actual hackers operate:
1. Reconnaissance
Ethical hackers gather intel. They scan for exposed servers, old logins, forgotten cloud buckets. Like someone walking around your house checking which doors are unlocked.
2. Scanning & Enumeration
Now they start poking. What versions of software are running? What’s open to the internet? They’re not breaking in yet—just checking the doorknobs.
3. Exploitation
This is the “break-in.” They use the intel to slip past a weak password, exploit an unpatched system, or trick an application into revealing too much data.
4. Privilege Escalation
Getting in is one thing. Taking control is another. Ethical hackers attempt to climb the ladder inside your network—just as real attackers would.
5. Reporting
Unlike criminals, they stop here. Instead of selling your data or planting ransomware, they hand over a detailed map of every flaw found, along with fixes.
Notice how it’s not just about tools. Sure, they’ll use scanners and scripts, but often the biggest wins come from human curiosity. A clever guess. An overlooked detail. That’s what makes ethical hackers so effective at mimicking real-world attackers.
Common Frustrations Companies Face
Here’s the thing—many businesses already think they’re secure. They’ve spent heavily on firewalls, VPNs, endpoint tools. But penetration testing often proves otherwise.
It can be frustrating to realize a single weak password or a misconfigured database could undo years of security investments. Or that a vendor’s sloppy coding left an entry point wide open. Ethical hackers shine a light on these uncomfortable truths, and yes, sometimes it stings. But it helps to build resilient security posture.
How CyberNX’s Penetration Testing Boosts Corporate Defences
CyberNX is leading, trusted and reliable cybersecurity firm, headquartered in India and presence in the US and the UAE. Their penetration testing service is designed to boost corporate defences with a trusted, comprehensive approach.
Some of the highlights include:
- As a CERT-In empanelled provider recognized by the Government of India. CyberNX thus brings credibility and assurance to businesses that demand the highest standards.
- The service blends the best of human expertise and automation to deliver accurate, real-world insights across all types of penetration testing. This ranges from web and mobile apps to networks, cloud, APIs, and IoT.
- Serving diverse industries like BFSI, healthcare, fintech, and manufacturing.
- CyberNX’s team of certified experts ensures vulnerabilities are uncovered and fixed before attackers can exploit them.
Conclusion
Look, cyber threats aren’t going away. If anything, they’re multiplying. Every day brings news of ransomware, insider threats and new zero-day exploits.
But there’s good news: you don’t have to face it blindly. With ethical hackers running penetration testing, you get a controlled preview of how attackers would target your organization. You see your weaknesses before they do.
And while it may feel unsettling to “invite” hackers in, remember—they’re on your side. They’re the ones keeping your glass house standing strong. And you can rely on trusted pentesting service providers like CyberNX.
FAQs
How often should a company conduct penetration testing?
It depends on your business environment. Most experts recommend at least once or twice a year, but companies that frequently update their applications, move workloads to the cloud, or handle sensitive customer data may benefit from quarterly testing. The key is simple: every major system change is a new reason to test.
Do ethical hackers use the same tools as cybercriminals?
Yes—and no. Ethical hackers often use the same scanning tools, exploit frameworks, and scripts as attackers because that’s what makes the test realistic. The difference? Ethical hackers stop short of causing damage. Instead of stealing data or disrupting systems, they document findings and provide remediation steps.
Can penetration testing disrupt business operations?
It can, if not planned properly. Some aggressive techniques may slow down systems or trigger alerts in production environments. That’s why ethical hackers work closely with internal teams, define clear scopes, and often use test environments to reduce risks. Done right, testing strengthens defences without interrupting day-to-day operations.
Is penetration testing only for large enterprises?
Not at all. Cybercriminals don’t discriminate by company size. In fact, small and mid-sized businesses are often targeted more because they lack robust defences. Penetration testing can be scaled to fit the size and complexity of any organization, making it just as valuable for startups as it is for Fortune 500 companies.







